SOC ALPHA 2
Difficulty: Medium
Q1) Hunt 1 (1/3) - What is the IP address from which the suspicious brute force traffic is seen? (Format: X.X.X.X)
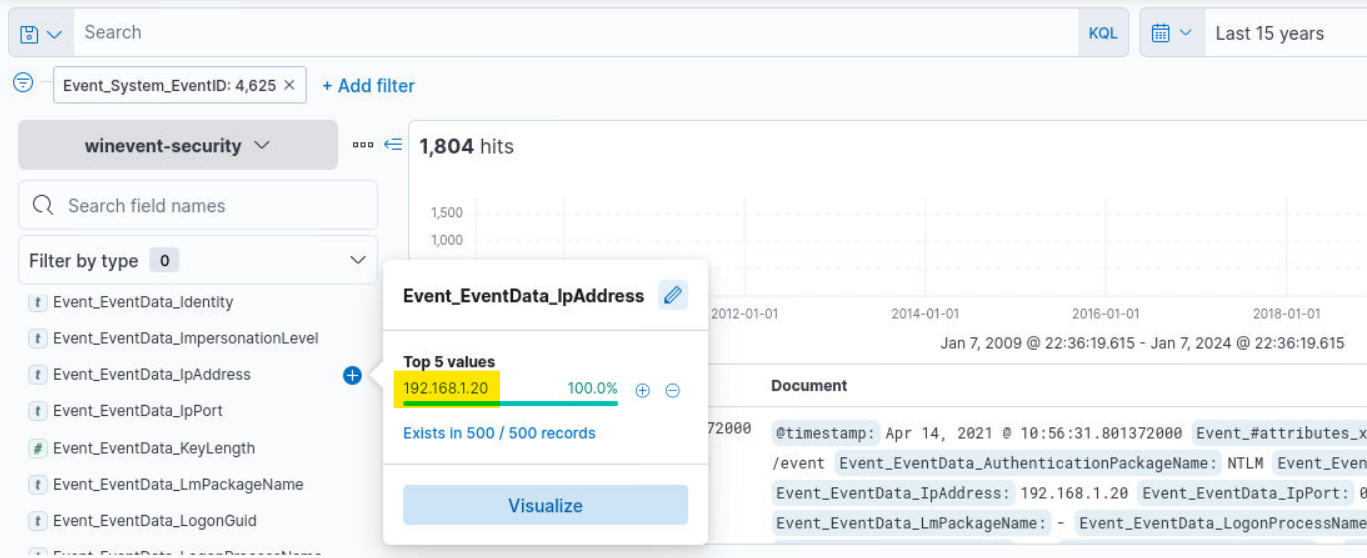
Answer
Q2) Hunt 1 (2/3) - What is the observed logon type? (Format: Logon Type Name)
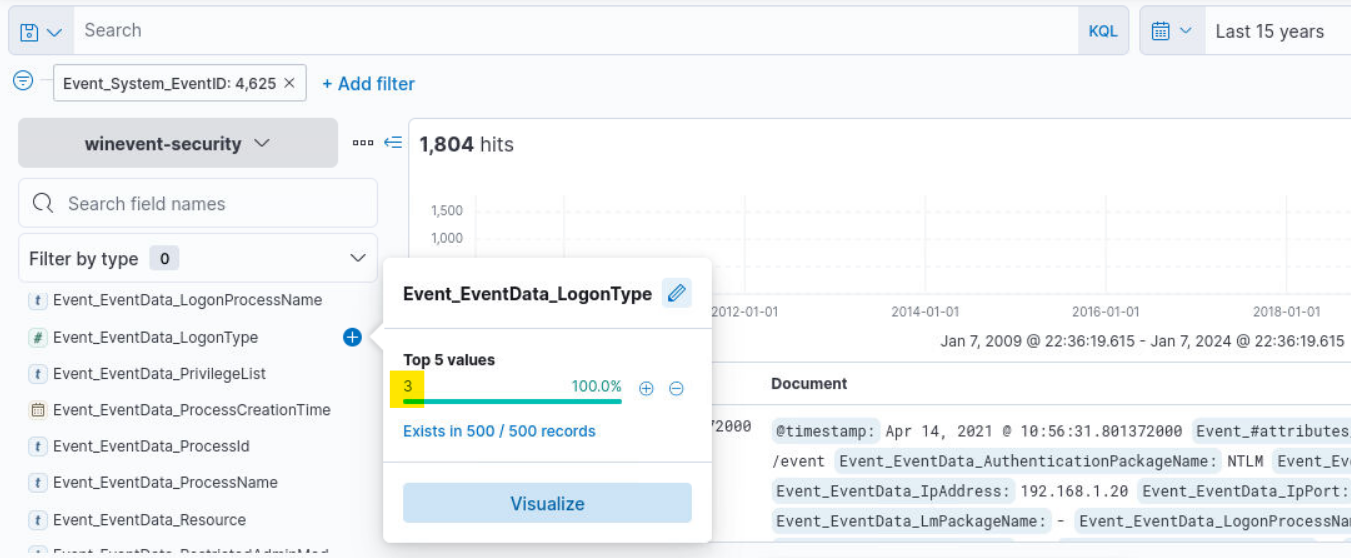
Answer
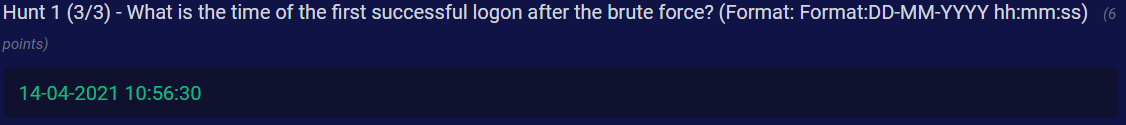
Q3) Hunt 1 (3/3) - What is the time of the first successful logon after the brute force? (Format: Format:DD-MM-YYYY hh:mm:ss)
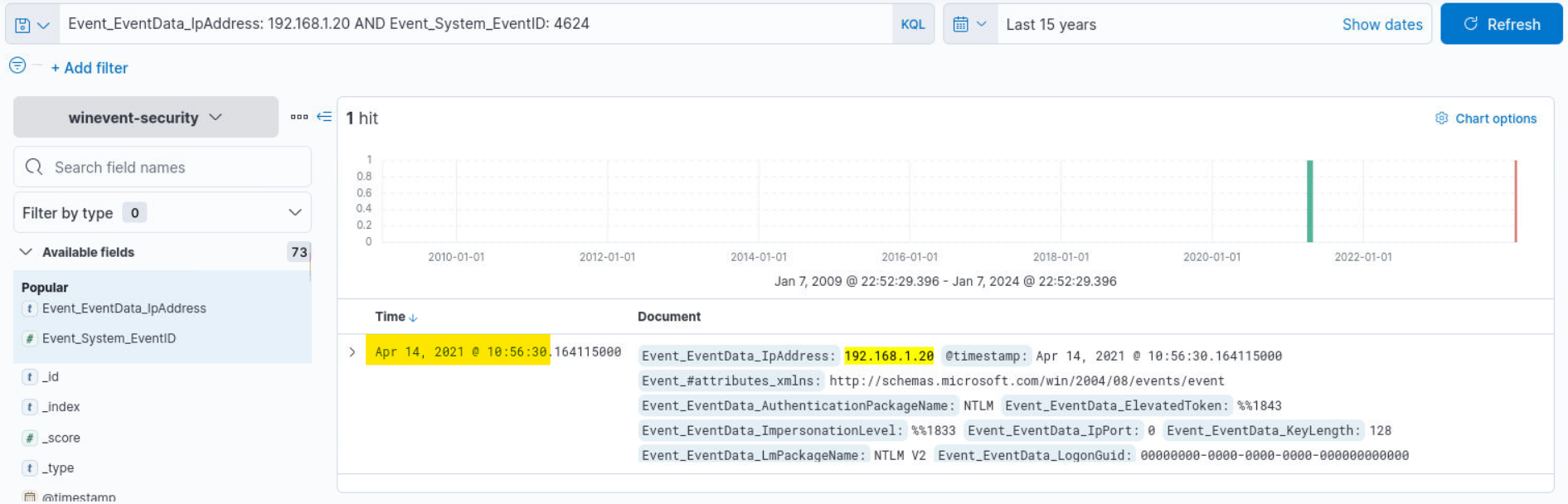
Answer
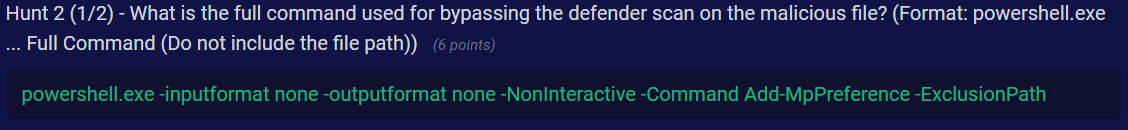
Q4) Hunt 2 (1/2) - What is the full command used for bypassing the defender scan on the malicious file? (Format: powershell.exe ... Full Command (Do not include the file path))
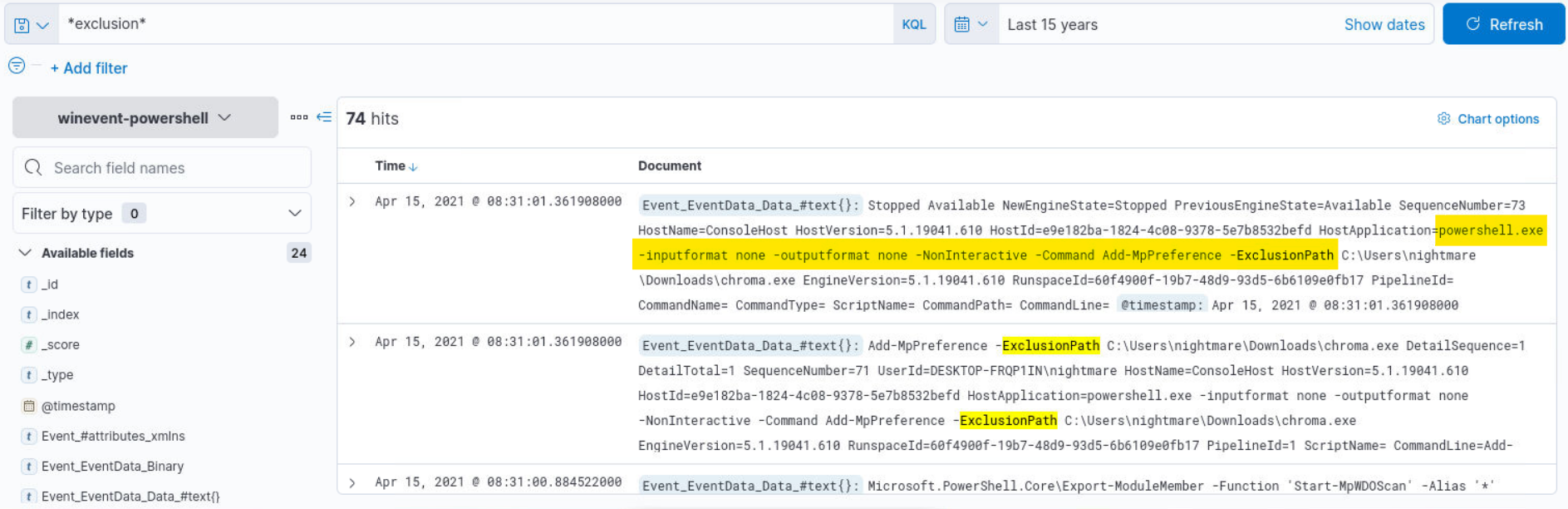
Answer
Q5) Hunt 2 (2/2) - What is the filename of the malicious application? (Format: filename.extension)
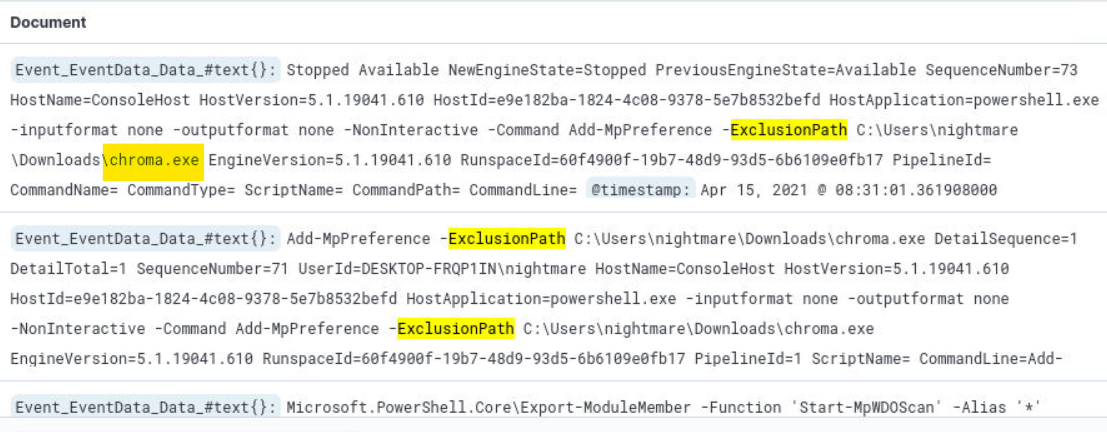
Answer
Q6) Hunt 3 (1/2) - What is the domain name? (Format: domain.tld)
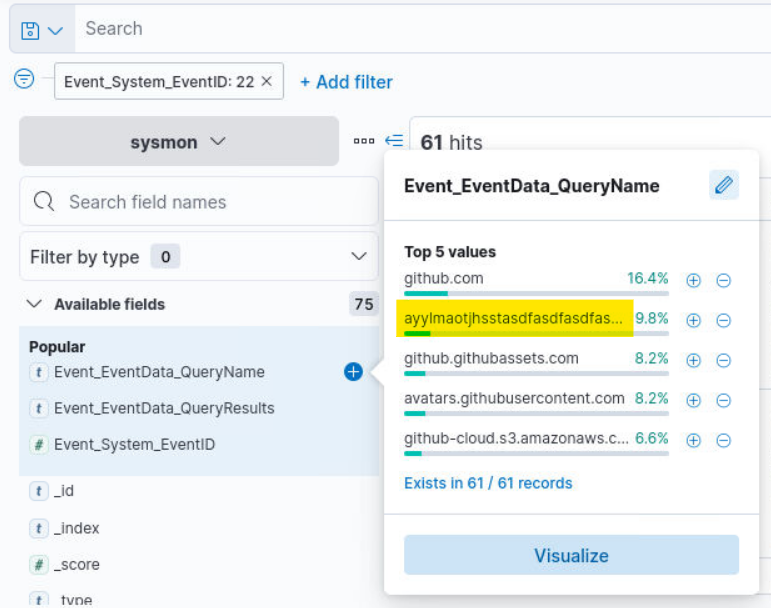
Answer
Q7) Hunt 3 (2/2) - What is the Execution ProcessID and ThreadID? (Format: pid, tid)
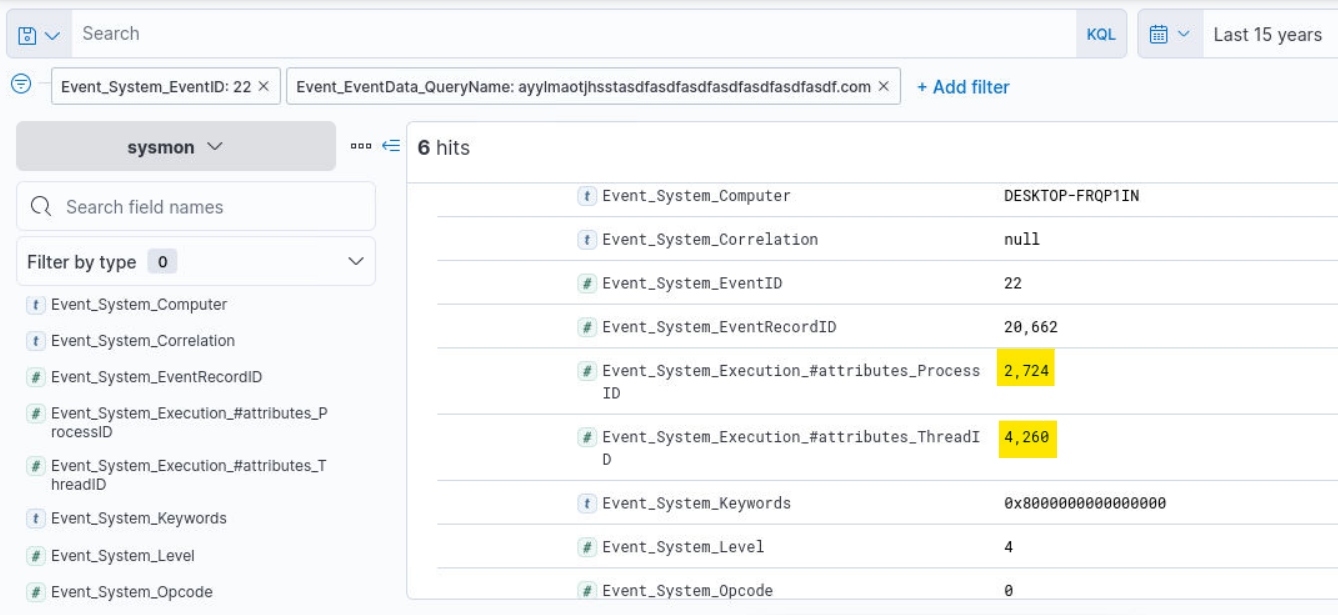
Answer
Q8) Hunt 4 (1/1) - What is the full path of the exe used for dumping password? (Format: C:\path\to\file.extension)
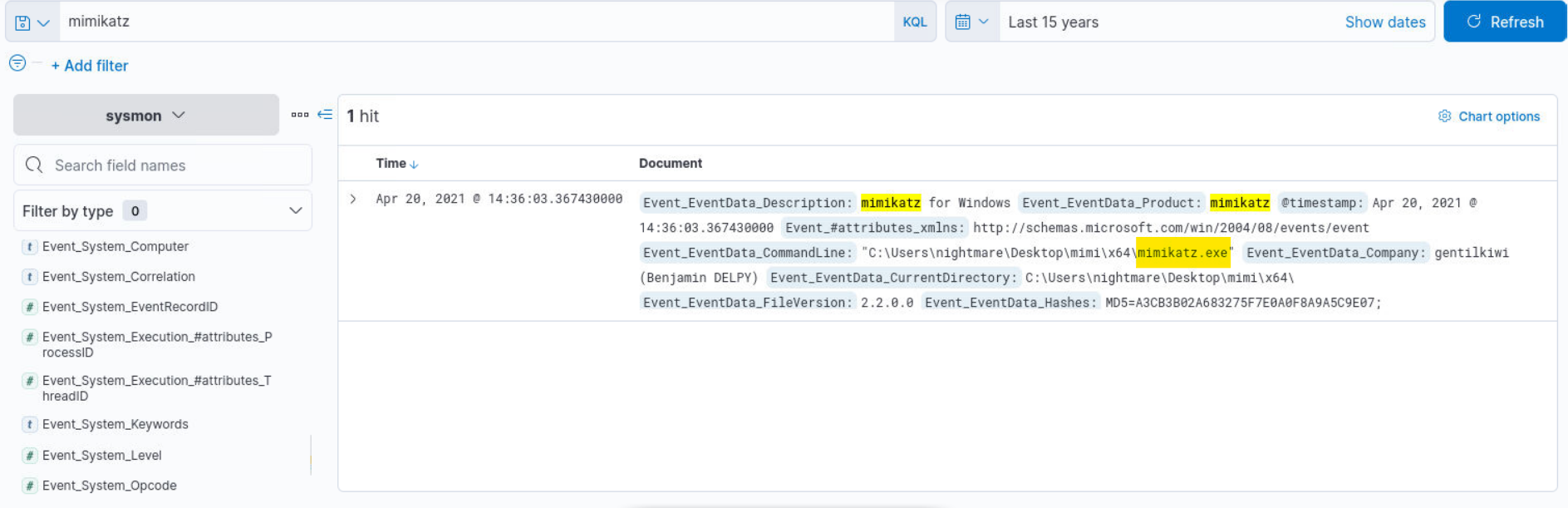
Answer
Last updated